How to protect Website from Cyber Attack
Today morning, I came across the news that a software engineer girl from Navi Mumbai was duped of Rs 73 lakh by internet fraud (e-fraud). It is evident that anything which is connected to the internet is vulnerable in the end. Hence, if you are not aware of security measures then you can be the next target of hackers.
Before diving into the solution, let’s understand the problem.
What is Cybersecurity?
Cybersecurity is an umbrella term that involves various tools and techniques to protect several digital components such as data, network and computers from unauthorized third parties.
Why is Cybersecurity important?
Digital economy plays an important role in the global economy. Cyberattack or malicious activity can lead to reputational and financial losses in a company.
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.” –Stephane Nappo
Generally, the primary objective of hacking is to get benefit from the victim as web attackers can ask for ransom. Moreover, in the corporate world, competitors hire hackers to slow down the websites of leading corporations. Therefore, web security is one of the most essential and difficult aspects to every organization which is linked to the internet.
How many types are Cyber Threats?
Here are some the most common types of Cyber Threats
· Cyberterrorism
· Malware
· Phishing
· SQL Injection (SQLi)
· Man-in-the-Middle Attack (MITM)
“Cyberterrorism” as the word defines itself: it is an awful illegal act in which skilled hackers cause massive destruction to the population, economy and environment of targeted territory with the help of the internet and technology.
Mostly, attackers target infrastructure systems to intimidate a government or section of population.
For instance: On 12 October 2020, Maharashtra State Electricity Grid (MSEG) was attacked by a Chinese state-sponsored hacking group called Red Echo which caused massive grid failure in Mumbai and surrounding areas for two hours.
Malware is a malicious software which is used for data breaching and disruption of computer functioning.
Here is the most common type of malwares

Phishing is a most popular type of social engineering. Attackers use fraudulent email, social media messages and text messages to get sensitive information like account number, login credentials, credit cards information from target.
They impersonate a real user or real website so users click on the provided link.
In September 2020, hackers sent a phishing email attempting to steal Amazon users credit card information.

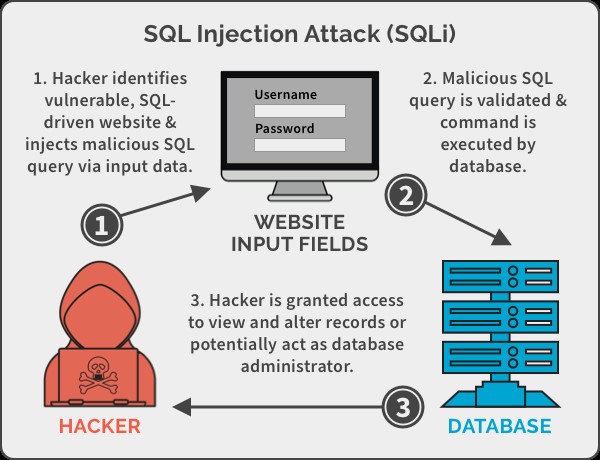
Structured Query Language (SQL) is a database language designed for data management and data retrieval.
In SQLi, attackers use a string of malicious code to get unauthorized access to web applications. They can steal and manipulate sensitive company data and customers’ personal details.
LinkedIn was hacked by a Russian hacker Yevgeniy Nikulin on 5 June,2012. He stole passwords of nearly 6.5 million user accounts.
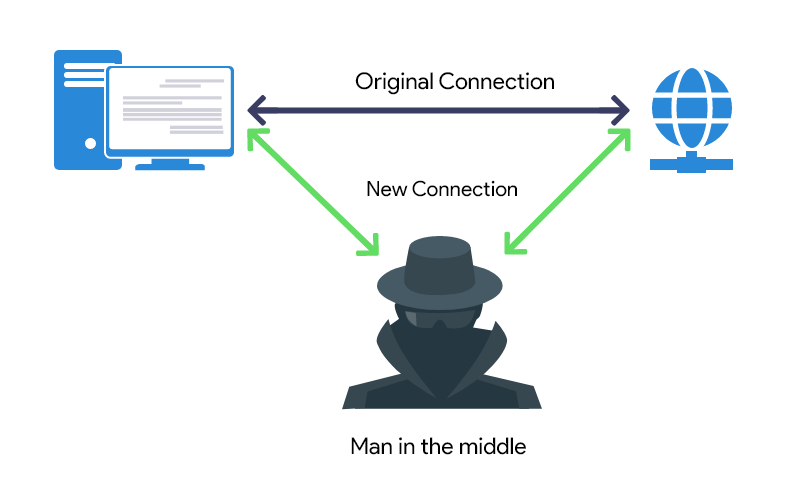
Man-in-the-Middle Attack (MITM)
It is just like your neighbor who eavesdrops on others private conversation without their consent.
Attackers install a packet sniffer to discover insecure network traffic and once a user logs into the insecure website. Hackers send them to fake websites which mimic the original website and collect all the sensitive data.
· IP Spoofing
· HTTPS Spoofing
· DNS Spoofing
· ARP Spoofing
· E-mail Hacking
· Session Hacking
· Wi-fi Eavesdropping
· SSL Stripping
How can you achieve Cyber Security?
There are various tools and technologies available to secure a website from web demons.
· Keep your Software update
· Strong password is mandatory
· SSL / TLS, HTTPS
· Firewall
· Secure Hosting
· Regular Backup
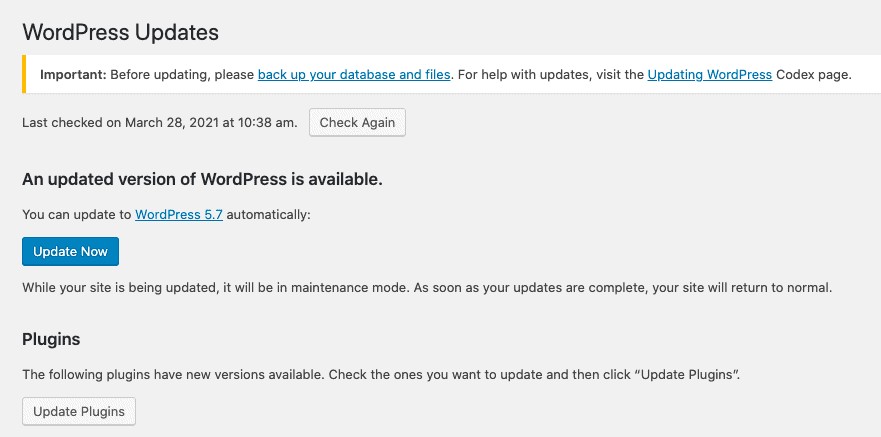
Keep your Software update
Software updates are vital for the health and security of websites.
If your website software and applications are not up to date then they are not secure.
Bots always search for outdated and insecure websites for exploitation. Therefore, take seriously all the update requests related to software, plug-ins, content management system, apps, and any scripts.
To monitor regular updates in a WordPress website, you can consider WP Updates Notifier.
Strong password is mandatory
“Passwords are like underwear: don’t let people see it, change it very often, and you shouldn’t share it with strangers.” – Chris Pirillo
There are some measures to qualify a strong password
· Opt long password (more than 6 letters) with small and capital case alphabets, numbers and special characters (#, $, @, &)
· Don’t use family members’ names, birthdays, pet names or any type of personal information.
· Avoid reusing the same password for various websites and login accounts.
· Update password frequently and create a unique one every time.
In market, several credible password managers are available which provide high level security and data backup services.
For WordPress website, use plugin Password Policies Manager for WordPress to enforce strong passwords. This plugin provides a one-click password reset policy in case of suspicious activity.
SSL (Secure Sockets Layer) / TLS (Transport Layer Security), HTTPS
Padlock icon next to the URL in the address bar denotes SSL/TLS protection of the website. SSL converts HTTP (not secure) into HTTPS (secure).
TLS is an advanced version of SSL in terms of security. It provides confidentiality, authenticity and integrity combinedly.
TSL encrypts the internet traffic and protects web applications against data tampering and eavesdropping.
For authentication, TSL verifies the client and server both to prevent data spoofing and other cyberattacks.
You can get an SSL/TLS certificate from a trusted third-party organization called CA (Certificate Authority). They digitally sign the certificate with a private key which verifies the clients’ devices.

Firewall
A Firewall is a security system which acts as a barrier between trusted and non-reliable networks. It allows and blocks network traffic according to predefined security policies.
Firewall guard device at entry point by analyze the incoming data traffic and filter out malicious sources to prevent attack.

Types of Firewalls
There are basically three types of firewalls based on their structure-
· Software Firewall (Host Firewall)
· Hardware Firewall (Appliance Firewall)
· Both
Software Firewall (Host Firewall) – Installed in each device and it monitors and regulates traffic through port (entry point).
Hardware Firewall (Appliance Firewall) – Installed between network and gateway. Very useful equipment for medium and large organisations, in which team members work on manifold computers under the same network.
While other firewalls are techniques which you can set up as software or hardware.
· Packet-Filtering Firewalls
· Next- Generation Firewalls (NGFW)
· Proxy Firewalls
· Circuit-Level Gateways
· Stateful Inspection Firewalls
· Cloud Firewalls
You must know basic measures of secured web hosting if you are planning to buy a storage space for website data. Because, the hosting environment is directly proportional to overall cyber security.
Evaluate the security features of different hosting provider companies and choose the host that provides server monitoring, two-factor authentication, malware detection, attack protection, and integration with security add-ons.
The companies’ data centers where the servers are physically located should have controlled access points, motion detectors, security cameras, and secure cabinet racks that prevent attackers from distressing the servers.
Here is some most secure web hosting services:
· Bluehost
Regular Backup
In a devastating situation, regular backup can save you from losing your sensitive data. Choose a reliable backup plugin that can restore your website because manual backups are time consuming and exhaustive activity.
List of best WordPress Plugins:
· BackWPup
· WPVivid
Conclusion
Being a web developer or entrepreneur, web security is an important practice of website development. A momentary loss of carefulness can cause catastrophic situations for your website data and it can be worse for any ecommerce website. Because bad actors can hack the customers personal details, bank account and credit card details. It can ruin your reputation among the users and stakeholders and lead to monetary losses. Therefore, above mentioned tools and techniques will be a lifesaver for your website.
2 Comments
Wilfred
September 14, 2022
It is not my first time to go to see this site,
i am browsing this web page dailly and obtain nice information from
here everyday.
locask
September 30, 2022
Good post! We will be linking to this particularly great post on our site. Keep up the great writing